Below is our recent interview with Syed Abdur, Director of Products at Brinqa:

Q: This is the first time we have spoken. Can you provide a brief overview of Brinqa?
A: Yes, I am happy to. Brinqa is a Cyber Risk Management company based out of Austin, Texas. We pride ourselves in delivering a unique risk centric and knowledge-driven approach to address crucial cybersecurity controls such as vulnerability management, application security, and cloud and container security. We see these as a subset of a wider category of critical Cyber Risk Management challenges that enterprises must plan for and address.
Brinqa was founded by cybersecurity industry veterans Amad Fida and Hilda Perez. In their extensive experience working with enterprise cybersecurity customers, one thing that struck both of them was the increasing complexity of enterprise technology ecosystems and the cybersecurity infrastructure charged with protecting it. They founded Brinqa to address the urgent need for a solution to connect and synchronize siloed cybersecurity products, processes and teams towards the unified goal of reducing cyber risk and improving an organization’s cybersecurity posture.
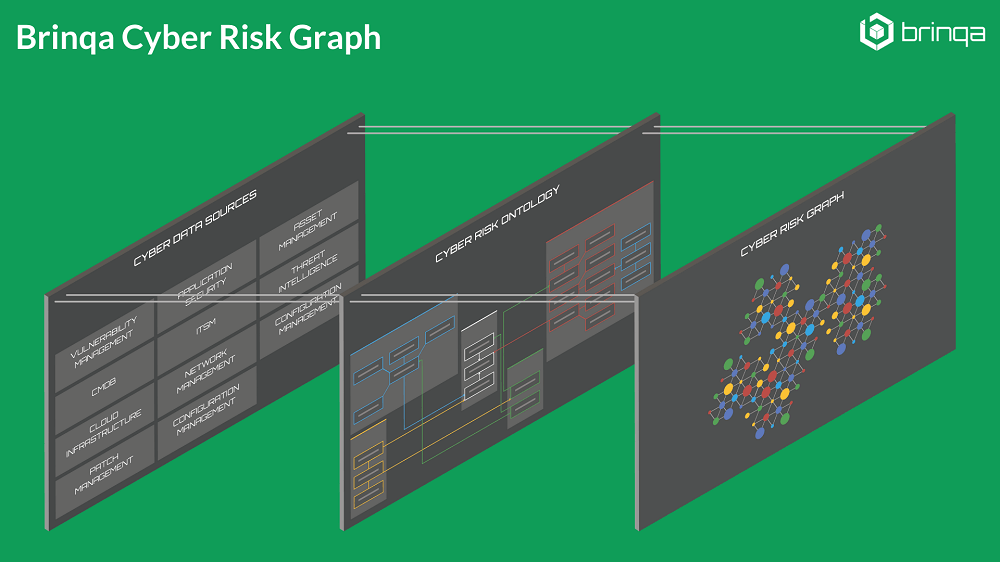
The result is the industry’s first Cyber Risk Graph — a Knowledge Graph for cybersecurity that provides a real-time representation of an organization’s infrastructure and apps, delineation of interconnects between assets and to business services, and a unified knowledge source for cyber risk decisions.
 Recommended: CompTrak – A Compensation Management Solution That Brings Incentive, Equity, Merit Review And Total Rewards Into A Single Platform
Recommended: CompTrak – A Compensation Management Solution That Brings Incentive, Equity, Merit Review And Total Rewards Into A Single Platform
Q: You mentioned “Knowledge Graphs.” Some readers might be familiar with these in context of Google Search. Can you elaborate on what Knowledge Graphs are, and how they relate to your solutions?
A: Knowledge Graphs are the information architecture behind Google search. When you search for a term on Google, you see an index card on the right with a list of things related to the search term. Google is able to present these results at a moment’s notice because they have already built a gigantic knowledge graph of all the information in their database and, more importantly, the relationships that exists between all of that data. Google Search was the first to employ Knowledge Graphs but since then they have seen adoption in other prominent technologies. Facebook has its “Social Graph.” LinkedIn has its own implementation of a Knowledge Graph. The common thread between these technologies is Data. Not just volume, but also the complexity of the information. These datasets are always changing and the mechanisms to collect, represent and analyze this information to create true knowledge have to automatically adapt.
There are four key characteristics that define Knowledge Graphs. These are also rules that govern all Brinqa applications.
The first characteristic is that the underlying data structure of a knowledge graph is an actual graph. A Knowledge Graph is a collection of nodes and relationships, with context at every level that imparts meaning to the data. This is important for the ability to traverse and operationalize any relationships that exists between two pieces of information or facts. In context of cyber risk management, this serves to ensure that any information that is relevant to risk analysis, regardless of where it exists in the organization, is easily referenced, accessed and incorporated.
The second characteristic is that Knowledge Graphs are semantic. Knowledge Graphs follow a well-defined ontology, differentiating them from data lakes (and other data stores) where there isn’t a strict structure and definition to the way data is interpreted, stored and represented. Underlying Brinqa’s Cyber Risk Graph is a comprehensive cybersecurity data ontology, which defines the different types of entities and their interrelations in scope for risk analysis. This includes assets such as network devices, applications, cloud instances, containers, IoT, etc., as well as vulnerabilities, alerts, notifications, and gaps — all correlated to cybersecurity controls. This provides control over how data from various tools, programs and processes comes together and is represented in a unified knowledge source.
The third characteristic is that Knowledge Graphs create new knowledge and insights. A Knowledge Graph is not just a mechanism for storing information. It is a source of new knowledge created by analyzing and transforming the represented data. In context of cybersecurity, a Knowledge Graph discovers and delivers insights to support critical decision-making. These insights were previously impossible to realize due to siloed information and disconnected business, IT and security processes.
The fourth, and maybe the most important, characteristic of a Knowledge Graph is that it is alive. The data ontology that defines the structure of information within a Knowledge Graph is completely dynamic and constantly changing. As information changes in the outside world, a Knowledge Graph evolves to represent that information accurately. This is crucial for today’s cybersecurity solutions to keep pace with the break-neck speed of change in enterprise technology.
Q: What led Brinqa to the decision to build a Knowledge Graph for cybersecurity?
A: We were very fortunate that early in the life of Brinqa we came across several customers and prospects that forced us to rethink and evolve our understanding of the cyber risk management problem. One such example, early on, that has had a lasting effect on our design philosophy is a customer that was using Brinqa to address cyber risk management for their network infrastructure. Due to some internal reorganization, the primary sponsor of the project was also made responsible for the security of the various physical sites managed by the organization. Building upon their cyber risk management program, they wanted to take a similar data-driven approach to the challenge of physical security. Familiar with our platform and its data modeling capabilities, they asked us to create a risk model for the problem – right down to tracking the risks associated with individual fire extinguishers. While this was clearly an edge case, and we didn’t anticipate coming across many customers with the same need, the limitations on the platform at the time to address this challenge forced us to think long and hard about our solution. Although our platform was already fairly dynamic and designed to handle a variety of cyber risk scenarios, we realized that we were still making a lot of assumptions about how organizations architect their technology infrastructures.
For Brinqa to be able to deliver a solution that could adapt to the rapid evolution of enterprise technology and evolve to fit all the unique ways in which organizations architect their technology and security infrastructure, our platform had to evolve. This resulted in a complete re-architecture of our platform and the underlying technology stack – a big part of which was the move from traditional relational databases to Neo4J, a graph database. Since then, we have tried to build “graph architecture” into every aspect of our product philosophy and discovered Knowledge Graphs on the way. These decisions have served us well since those early days, as our solution has seamlessly evolved from cyber risk management for traditional network infrastructure to application security, operational technology, IoT, and cloud-native technologies like IaaS, SaaS, and containers.
Q: Brinqa has recently earned accolades and industry recognition in the area of Vulnerability Management. What is unique about your approach to this problem?
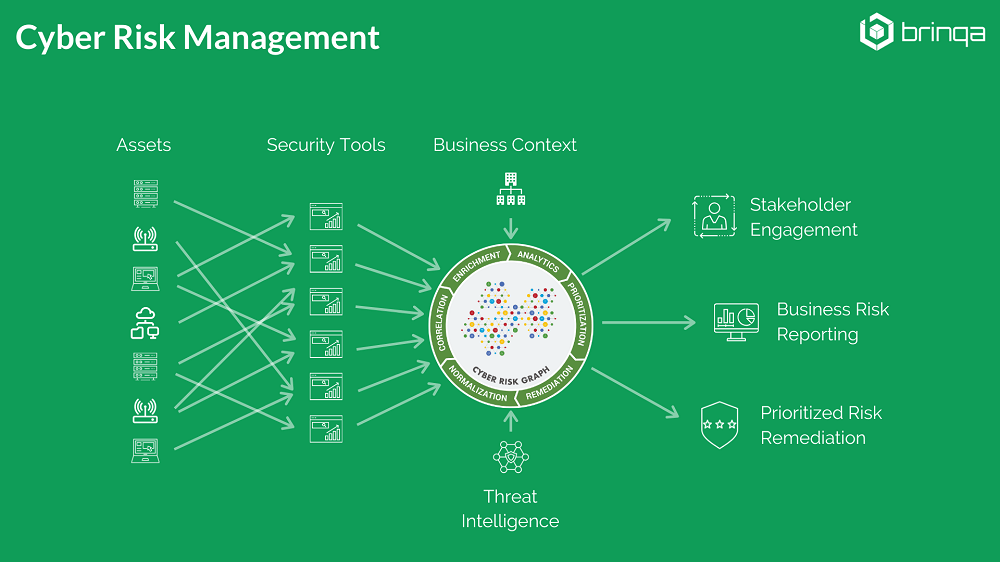
A: We have been honored to receive recognition from many respected industry publications, including Cyber Defense Magazine, CEO World, American Security Today, Cloud Computing Magazine, and SC Magazine, to name a few. What we find resonates most with our customers, as well as industry experts, is the understanding that to effectively manage vulnerabilities, it is crucial to identify, prioritize, and remediate the vulnerabilities that pose the biggest threat to each individual organization. Given the massive volume of vulnerabilities that exist in any enterprise technology environment, it is practically impossible to fix everything. As each business and IT infrastructure is unique, an effective vulnerability management program incorporates all risk factors that are relevant to the organization. Brinqa’s Cyber Risk Graph makes is easy for organizations to do so.
Brinqa customers often see vulnerability management as the springboard to wider, more comprehensive cyber risk awareness. Brinqa Vulnerability Risk Service gives customers everything they need to kick-start the creation of their cyber risk management program by making their vulnerability management program risk-aware with packaged connectors, risk models, standard risk scoring, remediation workflows, dashboards and reporting. However, most Brinqa customers quickly expand the scope to include application security, configuration management and identity and access management. Establishing a consistent cyber risk strategy that spans all security solutions and attack surfaces brings teams together to turn their knowledge-driven insights into targeted, automated and tracked outcomes that vastly improve the company’s overall security posture.
Q: Is this similar to your experience with Application Security, another one of Brinqa’s primary solution areas?
A: Application security is another area where a unifying force like the Brinqa Cyber Risk Graph pays huge dividends. With the advent of digital transformation, an ever-increasing number of business functions and processes now depend on software applications. These business applications vary greatly in significance and usage — from mission critical applications necessary for an organization to deliver its products and services, to trivial ones that support common day-to-day work. The sources of these applications vary greatly as well – from being procured from external vendors to being developed in-house. Application infrastructure itself is never static. It is constantly evolving with software being upgraded and integrated with an ever-changing collection of systems, some of which may belong to other business entities.
To evaluate application risk effectively organizations must analyze information from various application assessment and monitoring tools and programs – SAST, DAST, IAST, SCA, Penetration Testing – effectively and with the knowledge of how these applications support and impact business functions. Brinqa Application Risk Service provides a comprehensive application security data ontology to automate normalization, correlation, and analysis of data from disparate application testing tools and programs. The included Brinqa connectors make it possible to easily collect and collate application asset, vulnerability, context and threat data. Brinqa Application Risk Service integrates the various relevant data sources into a single authoritative source of truth that can now be utilized by all stakeholders and decision makers for effective risk remediation. Data correlation and enrichment functions build the relationships between all the different data points in the ontology that highlight contexts necessary for informed decision-making.
Q: You see Vulnerability Management and Application Security as a subset of a wider Cyber Risk Management discipline. Can you elaborate on what Cyber Risk Management means to Brinqa?
A: In recent years, a new understanding and practice of Cyber Risk Management has emerged around concepts of data science, automation, and analytics. It relies on the automated collection and organization of business, IT, and security data into a unified knowledge source to drive informed cybersecurity decisions. This is a far cry from the manual, questionnaire-based risk assessments that come to mind for many InfoSec professionals when they think about “risk” in the context of cybersecurity. Besides accomplishing the goal of identifying and addressing the most critical, impactful and imminent risks in an organization’s technology environment, this modern interpretation of Cyber Risk Management delivers crucial benefits to organizations:
- Incentivizes organizations to create an accurate inventory of all their diverse IT assets.
- Provides visibility into IT infrastructure and processes, and their relation to business.
- Brings together business, IT and security as equal stakeholders in keeping the organization secure.
- Provides common language and communication channels for varied stakeholders.
Q: And, I have to ask, what can we expect to see from Brinqa in 2020?
A: 2020 is an important year for Brinqa with an upcoming major release of our platform. This release will deliver a brand new UI along with a host of features aimed at making the platform even more dynamic and extendable. As part of this effort, we are working to open up the backbone of our integration ecosystem to the public — the Brinqa connector development framework. We currently have more than 100 connectors to a variety of IT and security systems, with almost as many more connectors in queue for implementation. Opening the connector development framework to our customers and partners will allow us to expand our integration ecosystem at a significantly faster rate.
 Recommended: Meet Suuchi – A Next-Gen Supply Chain Solution For Apparel Brands And Retailers
Recommended: Meet Suuchi – A Next-Gen Supply Chain Solution For Apparel Brands And Retailers
Q: Thank you for your time. Is there anything you’d like to add before we wrap up?
A: Thank you for the opportunity to discuss what we’re doing at Brinqa. I would just like to say that we’re very excited to be part of a new and emerging cybersecurity discipline in Cyber Risk Management, and have great expectations for its potential to help solve some of the biggest InfoSec challenges. I would also encourage those of your readers that found this conversation informative, to check out Brinqa’s LinkedIn page where we discuss many of the ideas covered here in more technical detail.

