* – This article has been archived and is no longer updated by our editorial team –
Insignary, the global leader in binary-level open source software security and compliance, is unveiling the results from a recently completed, comprehensive binary code scan for known security vulnerabilities in Wi-Fi routers. The scans were conducted across a spectrum of the firmware used by the most popular home, small-to-medium sized business (SMB) and enterprise-class Wi-Fi routers. The findings show that while KRACK may be the newest and potentially most harmful WPA2 security vulnerability, the firmware offered by router OEMs contains numerous known security vulnerabilities that can be exploited by hackers.
“Firmware provided for home and business routers is posted on manufacturers’ websites and well-known, third-party download sites. By leveraging our binary scanning tool, our research and development team examined the firmware supplied by the most popular home and enterprise Wi-Fi router manufacturers. We were surprised to find that all of the router firmware contained security vulnerabilities, with some containing quite a few,” said Tae-Jin (TJ) Kang, CEO of Insignary, Inc. “While KRACK WPA2 is the latest Wi-Fi security vulnerability, it appears to be just the tip of the iceberg, compared to what currently exists in router firmware.”
 Recommended: Loyalty Marketplace Gift On Track To Reach 100,000 Loyalty Programs Into Their Technology Platform
Recommended: Loyalty Marketplace Gift On Track To Reach 100,000 Loyalty Programs Into Their Technology Platform
About the Study
During the last two weeks of November 2017, Insignary’s research and development team scanned 32 pieces of Wi-Fi router firmware offered in the U.S., Europe and Asia by more than 10 of the most popular home, SMB and enterprise-class Wi-Fi router manufacturers. The Wi-Fi routers examined were produced by manufacturers that include: ASUS, Belkin, Buffalo, Cisco, D-Link, EFM, Huawei, Linksys, Netis and TP-Link.
Following are some of the key findings:
· The binary scans indicate that the Wi-Fi router firmware sold by the top manufacturers contain versions of open source components with security vulnerabilities
· Interestingly, most models’ firmware contains “Severity High” and “Severity Middle” security vulnerabilities, meaning that the deployed products and firmware updates remain vulnerable to potential security threats.
· The examination shows that a majority of the models’ firmware makes use of open source components with more than 10 “Severity High” security vulnerabilities, while 50% of the firmware uses open source components containing “Severity Critical” security vulnerabilities.
· The firmwares’ open source components containing “Severity Critical” security vulnerabilities have been identified below. These results indicate a trend among vendors to not make use of the correct, up-to-date versions of these software components.
o WPA2 (KRACK) – Key reinstallation attack;
o ffmpeg – Denial of Service (DoS);
o openssl – Denial of Service (DoS), buffer overflow and remote code execution;
o Samba – Remote code execution.
· All of the firmware leverage busybox and samba by default, with more than 60% of which use openssl.
· Significant security issues arise from openssl, which should prompt vendors to consistently apply the latest patches or use the version of the software that contains the fix.
· This study demonstrates that much of the firmware does not utilize the correct, most up-to-date versions of the OSS components available.
 Recommended: Swrve Raises $25M Series D Funding To Help Its Clients Build Highly Effective Mobile Marketing Campaigns
Recommended: Swrve Raises $25M Series D Funding To Help Its Clients Build Highly Effective Mobile Marketing Campaigns
The open source community has created new versions of the components to address all of the previously listed security vulnerabilities. Vendors can employ these versions to prevent data breaches and subsequent litigations that can cause significant corporate losses. Interestingly, during discussions with various vendors, Insignary encountered one manufacturer who expressed a preference in maunually applying patches, line by line.
Though this ad hoc approach to addressing vulnerabilities may be used by others, it appears to be the exception, rather than the rule. Additionally, while this method may work, it is still recommended that firmware developers scan their binaries to ensure that they catch and address all known security vulnerabilities.
Insignary’s findings suggest two possibilities for the failure to use the correct component version by Wi-Fi router vendors. Either the home, SMB and enterprise-class router vendors do not consider these vulnerabilities worth addressing, or they do not use a system that accurately finds and reports known security vulnerabilities in their firmware.
 Recommended: DIMOCO Payment Services Delivers A Combination Of Payment Methods, And Tailored Industry-Specific Solutions
Recommended: DIMOCO Payment Services Delivers A Combination Of Payment Methods, And Tailored Industry-Specific Solutions
About the Tool Used to Examine the Wi-Fi Firmware
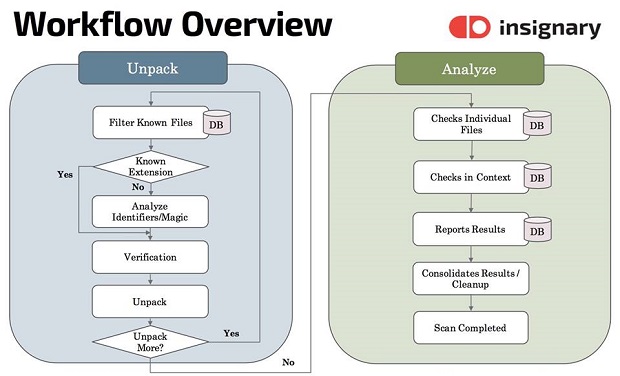
To effectively and accurately conduct this study, Insignary leveraged Clarity™, a security solution that enables proactive scanning of software binaries for known, preventable security vulnerabilities, while also identifying license compliance issues. It uses unique fingerprint-based technology, which works on the binary-level without the need for source code or reverse engineering. This makes it easy for software developers, value added resellers (VAR), systems integrators and MSPs overseeing software deployments to take proper, preventive action before software delivery.
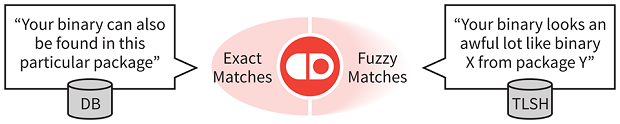
Insignary’s Clarity is unique in that it scans for “fingerprints” from binary code to examine and then compare against the fingerprints collected from open source components in numerous open source repositories. Unlike checksum or hash-based binary scanners, Clarity does not need to keep separate databases of checksum or hash information for each CPU architecture. This significantly increases Clarity’s flexibility and accuracy in comparison to legacy binary scanners.
Once a component and its version are identified through Clarity’s fingerprint-based matching, comparing them to more than 180,000 known security vulnerabilities catalogued in numerous databases, such as NVD and VulnDB, is straightforward. Clarity also adds enterprise support, “fuzzy matching” of binary code and support for automation servers like Jenkins.

