* – This article has been archived and is no longer updated by our editorial team –
ThreatModeler is the industry’s leading automated threat modeling platform, providing organizations a security solution which fully integrates into their existing development and DevOps toolsets and workflow. Through the ThreatModeler platform, organizations can improve their production outflow, gain real-time contextual awareness about their current threat portfolio and security level, and effectively reduce their overall risk posture. They recently introduced a new Partner Program to make their enterprise solution available through consultants and security vendors.
To learn out more about this new program, we sat down with Archie Agarwal, the Founder and CTO of ThreatModeler:

Q: What is threat modeling and how does it impact an organization?
A: A fundamental premise of defense, which military leaders have employed at least since the days of Sun Tzu, is that you can’t defend everything equally. While defenders are responsible for securing the entire system at all times, attackers only need to utilize one attack path at one point in time to be successful. Defenders, therefore, need to prioritize their resources and efforts. However, defenses need to be put in place before attackers attack. The vital question, then, is how defenders can most effectively determine the best way to prepare before attacks happen.
In the simplest terms, threat modeling is a systematic approach by which defenders may understand their system from the perspective and view of probable attackers. If defenders can understand how potential attackers are most likely to see and approach their system, they can prioritize their limited resources accordingly.
When applied to cybersecurity, threat modeling is used to identify potential threats and design flaws in applications, operational environments, devices, and systems as early as the initial whiteboarding stage. However, when done right, threat modeling can also be implemented across the organization’s entire cyber ecosystem, allowing real-time visibility into the organization’s current level of security through which organizations can effectively reduce their overall risk exposure.
Q: How exactly does the threat modeling process work?
A: There are three schools of thought when it comes to how to do threat modeling. The earliest threat models were created from data flow diagrams – a visual abstraction of how an application causes data to move through a computer system. By examining the diagram, security subject matter experts can deduce categories of potential threats and then determine possible mitigations.
More recently we’ve seen checklist-based threat models. These are very often used to ensure the minimum compliance requirements have been met. The underlying assumption of this approach is that if we comply with regulations and requirements, we’ve done what is “reasonably necessary” to secure our applications.
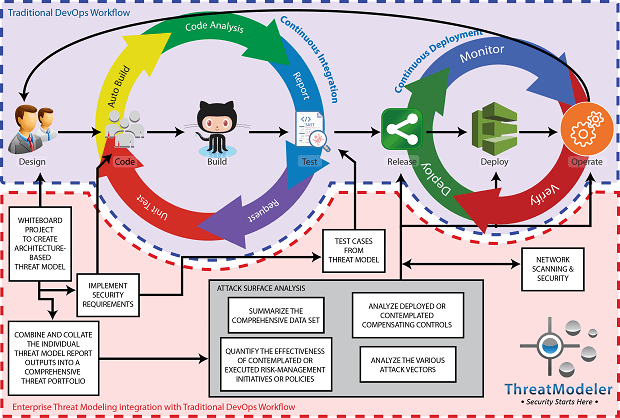
One of the significant downfalls of data flow diagram and checklist-based approaches is difficult to scale the process across the organization’s entire application portfolio because they rely on manual involvement by security experts. Such methods worked well enough when application production typically followed a waterfall method in which it would take months to produce a single product. However, in today’s fast-paced agile and DevOps production environments, production timelines are a couple of weeks or less, and updates and enhancements are integrated and deployed on a continuous basis. Modern threat modeling keeps pace and scales with production because the outputs are on a self-serve basis. Security expertise is encoded into a central threat library. As architecturally-based visual diagrams of the system or application being analyzed are created, the threat modeling platform automatically draws out the appropriate security expertise and includes it in the threat model outputs. Developers, operators, and QA teams working in a fast-paced environment then have the information they need for secure initial coding and deployment, even before the project is started.
 Recommended: Centage Corporation Provides Scalable, Cloud-Based Budgeting And Forecasting Solutions For Mid-Market Organizations
Recommended: Centage Corporation Provides Scalable, Cloud-Based Budgeting And Forecasting Solutions For Mid-Market Organizations
Q: What is enterprise threat modeling and in what way does it differ from more traditional approaches?
A: Traditional threat modeling was capable of analyzing a single application in isolation. By adding a second application and allowing for application interactions to the analysis becomes far too complicated for any practical usage quickly.
Enterprise threat modeling takes the process to a whole new level. As with traditional threat modeling, enterprise threat modeling starts with individual application threat models. However, enterprise threat modeling also allows building detailed threat models of on-premises or cloud-based deployment environments, IoT and embedded devices, industrial control systems, cyber-physical systems, endpoints, shared components, 3rd party systems, or anything else associated with the organization’s full cyber ecosystem.
Once as the number of individual threat models is increased, the organization’s understanding of their security and risk status increases dramatically:
• The ability to use one threat model as an architectural component in other threat models allows security teams to quantify the scope and impact of new relevant threats across the entire IT system in real-time;
• Security executives have high-level visibility into the organization’s threat portfolio and risk status, and can drill down to investigate the sources, the downstream impact, and assets exposed by any threat; and
• Security teams can perform dynamic ‘what-if’ analysis across the comprehensive attack surface to quantify the most efficient use of compensating controls.
 Recommended: Coinaccord Provides Full, Turnkey Solutions To Help Clients Launch, And Run Blockchain Products
Recommended: Coinaccord Provides Full, Turnkey Solutions To Help Clients Launch, And Run Blockchain Products
Q: How did you develop the concept for ThreatModeler?
A: I’ve worked in the cybersecurity industry for more than 20 years, helping Fortune 1000 companies with their threat and risk analysis and implementing secure software development processes. After observing the lack of scalable, automated solutions, I knew there had to be a better way to enable organizations to take a predictive approach to managing cyber threats and risks to their applications, information, and infrastructures. The concept was refined with industry feedback, and the first version of ThreatModeler™ was released in 2011. Over time the platform was matured, and the Enterprise Version was released in 2013.
Q: You’ve recently introduced a new partner program; could you tell us something more?
A: Until recently, the benefits of enterprise threat modeling were only available to Fortune 1000 companies. We recognized, however, that many smaller organizations – and even some global firms – increasingly outsource some or all of their cybersecurity function to consultants and 3rd party providers. Our Partner Program is designed specifically to allow these practitioners provide the best quality service to their customers on a scalable basis.
The Plan allows consultants and security firms
• Access to the ThreatModeler platform on a pay-as-you-go basis or to take advantage of enterprise bundling;
• To white-label the ThreatModeler outputs and include their branding; and
• To resell access to ThreatModeler to their customers.
Q: What are your plans going forward?
A: Threat modeling has become a need-to-have rather than a nice-to-have in today’s demanding and competitive IT environment. The threat landscape continues to evolve, and senior executives and their boards are beginning to understand both the seriousness of cybersecurity, but also that fully integrating security throughout all IT and production functions improves their bottom line. We are planning to roll out several innovations and product editions that will better serve our enterprise clients and partners to understand better and improve the security level of their full IT ecosystem, to quantify cybersecurity spend and results in terms the board can follow, and to reduce and manage residual risk.

